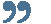Computer Security
Protect your information by securing your computer and business with a multi-dimensional, managed computer security service.
Global IT computer security services provide maximum protection, faster response and speed. Utilizing industry leading hardware and software technologies, our experienced security team are able to notify you of threats or viruses, before they enter your systems.


The Global Eye is a leading internet proactive monitoring system. It was developed by integrating industry leading, award winning security software's with in depth data center monitoring and alert systems with an always on, fastest possible mentality.
They proactively monitor network uptime and computer resources with automated notification. There are policies for the automation, procedures for governance and personnel to engage with clients prior to correction implementation.
- From $2.50 per month
- Proactive monitoring; partially or all systems, networks, resources and devices
- Operating 24 hours a day, 7 days a week, 365 days of the year
- Live Grid, provides real time proactive protection, detecting threats before they enter your system
- High malware detection
- Firewall
- Browser protection
- Light Footprint
- Attachment or program inspection
- Pattern signatures
- Behavior monitoring
- Blacklist lookup
- High performance
- Management administration console maintained by Global IT


Detect malware before it reaches your systems with leading proactive monitoring, and computer security protection. High protection against malware guaranteed, recognized by IT professionals worldwide.
- From $2.50 per month
- 25 years #1 leading software experience
- Live Grid, real time proactive protection
- Spam filtering levels and options
- Attachment or program inspection
- Blacklist lookup
- Pattern signatures
- Behavior monitoring
- High performance, fast, low resource impacting
- Management administration console
- Employee monitoring options
- Learn more


Cloud firewalls protect businesses before threats enter your business network. Having a firewall is just not enough. Businesses are adapting to a multi-layered protection approach. Maintaining and managing internet security successfully requires policies, routine maintenance and testing, monitoring, changes and adjustments in order to protect and secure business information. Incorrectly configured or out dated firewalls are becoming more common, and using different vendors or IT professionals adds increased security risk.
Having a qualified, trained IT service provider with technical resources and diverse experience will save businesses in unnecessary vendor costs, and protect from lost revenues by increasing productivity and securing business from the unnecessary risk.
- Cloud firewall options, UTM (Unified Threat Management)
- Firewall devices (Cisco, Juniper, Sonicwall, Fortinet, FreeBSD)
- Real time protection
- Monitors, alerts and logging (Netflow, NFSEN, Cacti)
- VPN, secure remote access
- Port forwarding, VLANs
- Hardware patches, updating
- Same day hardware replacement
- Day to day management, changes
As you grow and hire more staff, maintaining and implementing technology security policies is becoming increasingly more important. Loss of information, data or trade secrets can be devastating to any business and cause loss of revenues to competition or hackers prying eyes.
- Technology security assessment
- Technology vendor assessment
- Develop technology security policies
- Develop network security policies
- Develop personnel security policies
- Define rules and guidelines for exposure
- Define and maintain vulnerabilities
- Implement and manage the policies

Any business that stores, processes or transmits cardholder data is required to be PCI compliant. Like any compliance regime, PCI DSS can be complex and difficult to manage. The Payment Card Industry Data Security Standard (PCI DSS) outlines the best practices for securing credit card data that is stored, processed or transmitted. At Global IT we understand PCI compliance and how it can help you become more secure. We have services that cover every aspect of compliance, along with expert PCI vendors and staff to help you to navigate the process.
- PCI DSS compliant as a Service Provider and Merchant
- Auditing of systems for PCI preparation
- Monthly scanning of systems
- Remote Access Solutions
- Alerts and reporting
- Ongoing management, patches, updating
- Policy & procedure development


 Cyber black markets are a maturing, multi-billion-dollar economy, with robust infrastructure and social organization.
Cyber black markets are a maturing, multi-billion-dollar economy, with robust infrastructure and social organization.